Big Data: the Risks and Opportunities of AI in Cybersecurity
There has been a lot of fuss about big data, and on how the data streams have been increasing exponentially. In order to fully understand this massive digital growth, Cybersecurity Ventures has framed this by predicting, “the total amount of data stored in the cloud… will be 100 times greater in 2021 than it’s today”. Globally, digital content is expected to encompass 96 billion terabytes (96 zettabytes) by 2020.1
The big picture on big data and artificial intelligence
In an ever-connected world – the Internet of Things (IoT) will experience a ‘Big Data Big Bang’, where the sheer amount of online devices that might be online by 2020 is mind-boggling.2 It’s certainly not inconceivable that the global embrace of artificial intelligence (AI) has steadily been gaining traction. The link between AI and big data is apparent when you examine big data’s role in empowering AI.3
Cybersecurity Ventures has framed this by predicting, “the total amount of data stored in the cloud… will be 100 times greater in 2021 than it’s today.”
With this much, often confidential, data being produced – what is being done to protect it?
THE RISKS
AI is becoming a powerful force in organisations, especially in this digital age, due in part to technology unlocking the potential of big data with AI capabilities.5 If that thought doesn’t give you pause, it should. While AI can be used for good, it’s a tool – and conversely, it can also be used to commit harmful acts.
1. Privacy breaches
“It’s not just a coincidence that privacy issues dominated 2018. These events are symptoms of larger, profound shifts in the world of data privacy and security that have major implications for how organisations think about and manage both,” says Andrew Burt, Chief Privacy Officer and Legal Engineer at Immuta.6
The modern world is experiencing an overlap of privacy and security concerns where AI plays a big role in boosting the viability of both digital protection and cybercrime.8 Privacy is a top priority for businesses, especially now – whereas before, this was paramount to individuals. Big data has changed the availability of so-called private information, by making it at risk of data breaches. According to the 2019 Official Annual Cybercrime Report by Cybersecurity Ventures, sponsored by Herjavec Group, “Cybercrime is the greatest threat to every company in the world, and one of the biggest problems with mankind.”9
2. Cyber attacks
A cybercrime, cyber threat or cyber attack is an illegal activity involving a computer or a network-connected device like an iPad or cell phone.10 The cyber attacker or cyber hacker has the intention of gaining access to a network, stealing confidential data, using the computer as an accessory to a crime, or downloading software to a person’s device without their knowledge.

Steve Morgan, founder and editor-in-chief of Cybersecurity Ventures agrees, “Ransomware has emerged as the default mode of attack for cybercriminals in 2018.’’12
The different types of cyber hacking include:
- DoS attacks
- Drive-by downloads
- Malvertising
- Malware
- Man in the middle
- Password attacks
- Phishing
- Ransomware
- Rogue software
How AI is being used in cyber threats and cyber hacking
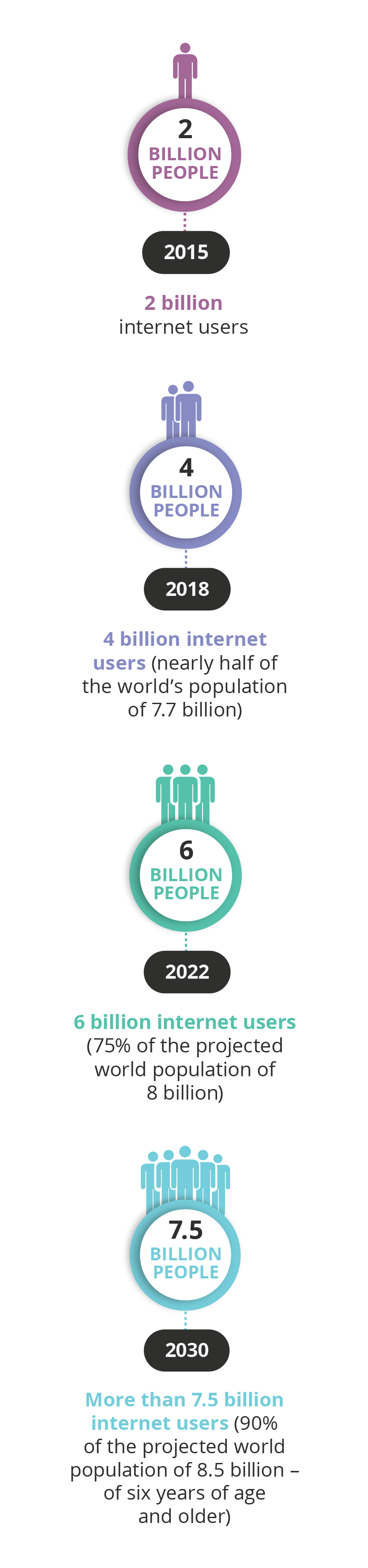
The threat of cybercrime is increasing, due to population growth and access to the internet:13
In 2017, artificial intelligence technology was detected by Darktrace Incorporated, in a cyber attack that occurred in India.14 What the malware managed to do was use AI to figure out normal user behaviour patterns used in the network; mimic the behaviour of the network, systems and the users of the system; and then hide in the background making it difficult to detect. Although the cyber attack was detected in the early stages, according to Chief Executive of Darktrace, Nicole Eagan, this is just the beginning – these are just the early signs of machine learning and artificial intelligence being used to attempt (and soon succeed at committing) cybercrimes.15
THE OPPORTUNITIES
1. AI can improve cybersecurity
Put simply, this is a practice concerned with the confidentiality and availability of information (such as data), as well as the protection of that information. The level of cyber protection needed depends on whether you’re dealing with an amateur cyber hacker or a dangerous criminal group. The good news is the emergence of using AI to combat cyber attacks could reinforce and improve cyber protection strategies – leading to businesses saving a lot of money.
As we work our way through the 21st century, it’s imperative for every business, whether they’re a small enterprise or a large corporation, to have a cyber protection leadership plan in place. “Cybersecurity has emerged as a hot commodity in the tech sector in 2018 thanks to fresh revelations, new regulations and a rise in data breaches.”16
As more people learn to utilize the benefits of AI, others are learning to exploit it by aiding cyber attacks. Harold Moss, Senior Director of Strategy and Business Development at Akamai Technologies, and a Guest Expert on the Cybersecurity: Managing Risk in the Information Age online short course from Harvard’s Office of the Vice Provost for Advances in Learning, in association with HarvardX, describes cyber threats like this:
“It’s almost like kidnappers – kidnappers watch where people go, and then they say ‘okay, I know this is a point where you’re going to be vulnerable, that’s where I’m going to get you’. Cyber hackers are no different.”
2. How AI is revolutionising risk management and digital protection
The extent of this cyber threat in the US is compared to an out-of-control epidemic.17 A supervisory special agent with the Federal Bureau of Investigation genuinely believes that all private data on US citizens has already been stolen through cybercrime, and is available for sale on the dark web18 – a notorious part of the internet that isn’t indexed by search engines, that illegally sells items to other criminals, which is only accessible through special software.
These types of private data could include:
- Links
- Networks
- Architecture protocols
- The state of network nodes
AI will possibly be the most effective tool for interpreting this data to continually identify present vulnerabilities and to consequently, take action to counterattack and prevent attacks in the future.19 Just two years on and we’re already seeing the use of AI to improve issues like risk management, and to detect anomalies, network cyber attacks, and malicious applications or software.
New AI algorithms use machine learning to adapt over time. The latest updates to malware and other cyber attacks have become difficult to detect using traditional digital security methods. As threats evolve, so should the security systems, as well as the individuals responsible for deploying these systems. By implementing the use of AI, digital security professionals will be able to free up a lot of their time to develop and improve current protection strategies. Chris Ganje, CEO and Co-founder of Amplyfi, a company offering products harnessing artificial intelligence and offering corporate strategic thinking, says:
“In cybersecurity, AI can automatically identify potentially malicious software behaviour, attack vectors and related anomalies in real time, allowing a continuously adaptive defence mechanism to identify and shut down intrusions faster and easier than ever before. This technological advancement not only significantly reduces the number of cybersecurity breaches, but also empowers analysts to better focus their time and speeds up the process to identify breaches from hundreds of days to mere hours.”20
Cybersecurity has emerged as a hot commodity in the tech sector in 2018 thanks to fresh revelations, new regulations and a rise in data breaches.
Four digital security companies utilising AI:
- SparkCognition
This US-based company creates artificial intelligence solutions to problems related to defence and cyber protection. SparkCognition offers DeepArmor, an antivirus product using AI to identify mutating viruses and detect new malware approaches.21 - Cylance
The company’s product line is based on the premise of blocking data breaches, and their product, CylancePROTECT uses AI technology to identify and stop malware. This unique product has an edge through “Predictive Advantage”, as it uses algorithms to determine how future cyber attacks will occur.22 - Appthority
This company focuses on mobile cyber protection and uses artificial intelligence by providing customers with a platform to automatically detect and grade suspicious behaviour like malware, intellectual property exposure, and corporate data security breaches.23 - BehavioSec
This behavioural biometric company monitors end-users’ keystrokes and mouse movements to create digital fingerprints. This form of security ensures continuous authentication, makes it easier to detect anomalies, verifies customers, and prevents cyber attacks and fraud. The artificial intelligence technology can be deployed on a cloud-based system or on-site.24
3. A rise in demand for digital security jobs
In 2022, you can expect a 1.8 million shortage of digital security professionals in the global workforce.25 The 2017 results of the eighth Global Information Security Workforce Study were surveyed from over 19,000 information security professionals worldwide. People holding IT jobs need to recognise that these positions, by necessity, also include digital security responsibilities. Examples of such duties include: protecting and defending apps, data, devices, infrastructure, and people. Making the need for working professionals with expertise in cyber protection, more in demand than ever before.26
Although the emergence of artificial intelligence in the field of digital protection is predicted by many to become a double-edged sword. Having a continually-evolving understanding of risk management and current cyber hacking trends, is imperative to distinguish the vulnerabilities of your organisation.
- 1 Morgan, S. (Dec, 2018). ‘Cybercrime damages $6 trillion by 2021’. Retrieved from Cybersecurity Ventures.
- 2 Morgan, S. (Dec, 2018). ‘Cybercrime damages $6 trillion by 2021’. Retrieved from Cybersecurity Ventures.
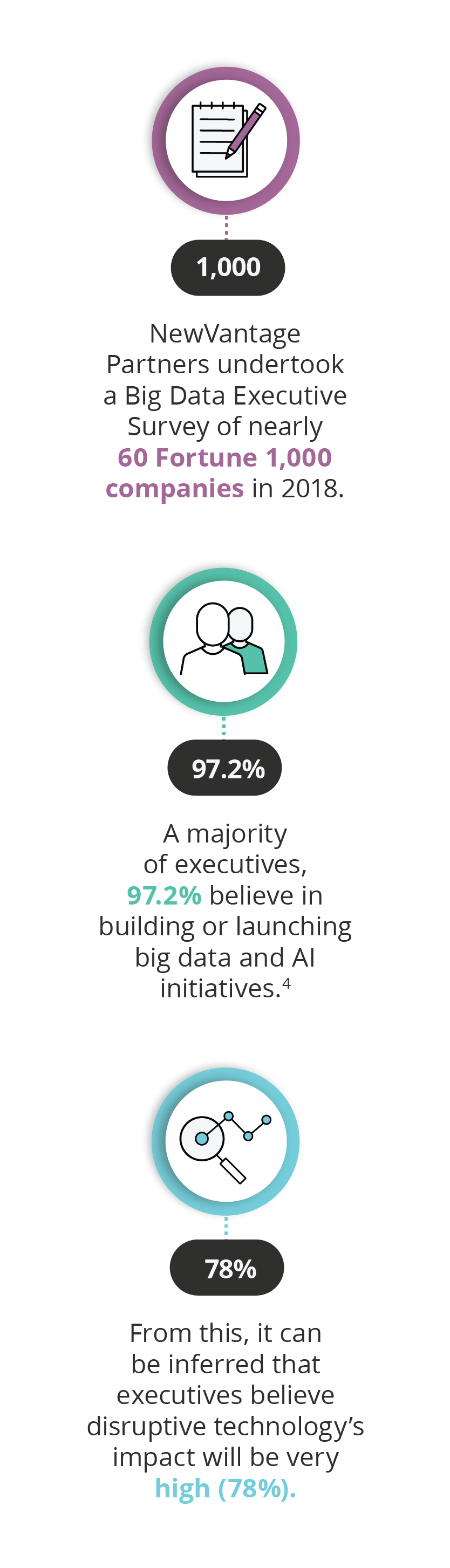
- 3 (2018). ‘Big Data Executive Survey 2018’. Retrieved from NewVantage Partners.
- 4 (2018). ‘Big Data Executive Survey 2018’. Retrieved from NewVantage Partners.
- 5 (2018). ‘Big Data Executive Survey 2018’. Retrieved from NewVantage Partners.
- 6 Burt, A. (Jan, 2019) ‘Privacy and cybersecurity are converging. Here’s why that matters for people and for companies’. Retrieved from Harvard Business Review.
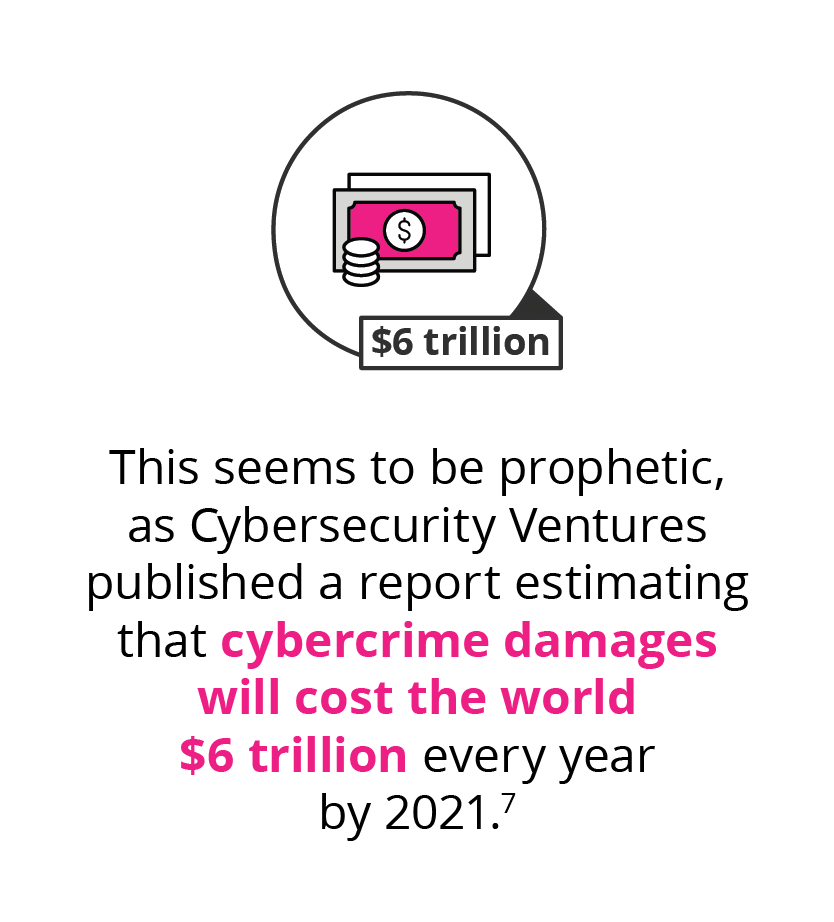
- 7 Morgan, S. (Oct, 2018). ‘Top 5 Cybersecurity Facts, Figures, Predictions, And Statistics For 2019 To 2021’. Retrieved from Cybersecurity Ventures.
- 8 Burt, A. (Jan, 2019) ‘Privacy and cybersecurity are converging. Here’s why that matters for people and for companies’. Retrieved from Harvard Business Review.
- 9 (2019). ‘The 2019 Official Annual Cybercrime Report’. Retrieved from Herjavec Group.
- 10 (2019). ‘11 ways to help protect yourself against cybercrime’. Retrieved from Norton by Symantec.
- 11 Yogesh, B. (Dec, 2018). ‘Cybersecurity trends 2018: Year of regulations and breaches’. Retrieved from Cybersecurity Investing News.
- 12 Morgan, S. (Dec, 2018). ‘Cybercrime damages $6 trillion by 2021’. Retrieved from Cybersecurity Ventures.
- 13 Morgan, S. (Dec, 2018). ‘Cybercrime damages $6 trillion by 2021’. Retrieved from Cybersecurity Ventures.
- 14 Norton, S. (Nov, 2017). ‘Era of AI-powered cyberattacks has started’. Retrieved from The Wall Street Journal.
- 15 Norton, S. (Nov, 2017). ‘Era of AI-powered cyberattacks has started’. Retrieved from The Wall Street Journal.
- 16 Yogesh, B. (Dec, 2018). ‘Cybersecurity trends 2018: Year of regulations and breaches’. Retrieved from Cybersecurity Investing News.
- 17 Morgan, S. (Dec, 2018). ‘Cybercrime damages $6 trillion by 2021’. Retrieved from Cybersecurity Ventures.
- 18 Guccione, D. (Jan, 2019). ‘What is the dark web? How to access it and what you’ll find’. Retrieved from CSO.
- 19 (February, 2018). ‘AI will underpin cybersecurity’. Retrieved from Cybersecurity Intelligence.
- 20 (February, 2018). ‘AI will underpin cybersecurity’. Retrieved from Cybersecurity Intelligence.
- 21 (2019). ‘Products’. Retrieved from SparkCognition.
- 22 SE Labs. (Mar, 2018). ‘Predictive malware response test’. Retrieved from Cylance.
- 23 (2019). ‘Mobile Threat Center’. Retrieved from Appthority.
- 24 (2019). ‘Solutions’. Retrieved from BehavioSec.
- 25 (2017). ‘2017 Global Information Security Workforce Study’. Retrieved from Centre for Cybersafety and Education (ISC)2.
- 26 Khoja, R. (Dec, 2017). ‘How AI is the future of cybersecurity’. Retrieved from Info Security Group.